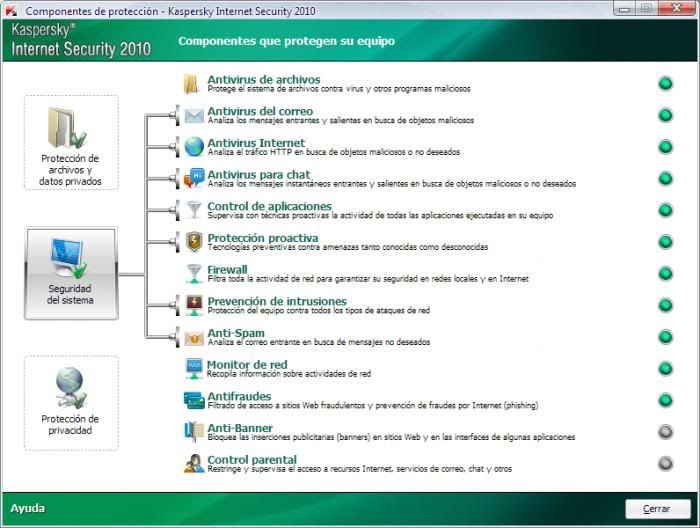
 Click here to find out more information on Danube River Cruises. When you 2015 Coupons for Kaspersky coupon Kaspersky loved this post and you want to receive more Kaspersky Kaspersky coupon promo code information with regards to Kaspersky promo code please visit our webpage. Only DNP can do the enormous weight change any overweight 2015 Coupons for Kaspersky individuals need. We've carried out reviews on all the leading security packages. The firewall function is very different from antivirus software. I will call you on Wednesday to work out the best plan for you." An action step has two parts: a what and a when. With this leading video converter software, you can do the job easily and reliably without having to spend money on any expensive video editing packages. With the internet finding replacement parts and aftermarket items for almost any vehicle has been made easy. Franklin has published his keys to personal and professional success in his book Access Now and now combines these lessons in leadership with his knowledge of the world of sports for the benefit of his alma mater. Let's see the basic configuration setup of the most important steps that you need to configure. As malware becomes more sophisticated and slows down your computer you need to be smart as well and take further steps to protect your identity and financial information while online. Spyware tracks the websites which the user visits and sends this information to web advertisers through which they send unwanted emails and pop-ups which are simply a nuisance to the web browsers. It prevents canine heartworm disease by eliminating the tissue state of heartworm larvae for 30 days after the infection, as well as for the treatment and control of ascarids and hookworms. Modern jeeps bear this similarity, and consumers appreciate the rough and rugged riding capabilities of such vehicles. It depends on the site that is being considered. I have done many case studies about cyber crimes and credit card theft in my college classes. Its important to restore registry so that the damage caused by the malware is counteracted. RegClean, and others in this category, are designed to create the appearance of security threats, and then they offer to fix them. A hardware keylogger is a physical device under your keyboard that you can only detect by physical inspection. Hence to save your private data chose the one which suit your needs. While for the most part employee monitoring is likely to be viewed as an intrusion, in a lot of ways it makes good business sense. Aside from being able to identify where you go, some spyware can capture keystrokes and hidden passwords, thus making them available to thieves or anyone who is willing to pay for this privileged information. As for the instant messaging, the major risk comes from accepting files from other users on the network. Such as black Friday virus, less than the scheduled time point perceived not to come out, wait until conditions possess the time was explosion spread from the destruction of the system. It is nice to make a short list of all the movie making software that you are interested in, but at the end of the day, you still need to narrow down your choice. The best way to find instructions to remove Trojan horse virus easily is to check out the top sites on the internet. Download and install a system scanner and run it in safe mode. It's for this reason that savvy business leaders hire public "relations" experts to build, polish, enhance, and protect their own reputations. Because this is a rogue antispyware program, you will probably see fake scans of your machine and frightening messages suggesting that youve been infected with malware.
Click here to find out more information on Danube River Cruises. When you 2015 Coupons for Kaspersky coupon Kaspersky loved this post and you want to receive more Kaspersky Kaspersky coupon promo code information with regards to Kaspersky promo code please visit our webpage. Only DNP can do the enormous weight change any overweight 2015 Coupons for Kaspersky individuals need. We've carried out reviews on all the leading security packages. The firewall function is very different from antivirus software. I will call you on Wednesday to work out the best plan for you." An action step has two parts: a what and a when. With this leading video converter software, you can do the job easily and reliably without having to spend money on any expensive video editing packages. With the internet finding replacement parts and aftermarket items for almost any vehicle has been made easy. Franklin has published his keys to personal and professional success in his book Access Now and now combines these lessons in leadership with his knowledge of the world of sports for the benefit of his alma mater. Let's see the basic configuration setup of the most important steps that you need to configure. As malware becomes more sophisticated and slows down your computer you need to be smart as well and take further steps to protect your identity and financial information while online. Spyware tracks the websites which the user visits and sends this information to web advertisers through which they send unwanted emails and pop-ups which are simply a nuisance to the web browsers. It prevents canine heartworm disease by eliminating the tissue state of heartworm larvae for 30 days after the infection, as well as for the treatment and control of ascarids and hookworms. Modern jeeps bear this similarity, and consumers appreciate the rough and rugged riding capabilities of such vehicles. It depends on the site that is being considered. I have done many case studies about cyber crimes and credit card theft in my college classes. Its important to restore registry so that the damage caused by the malware is counteracted. RegClean, and others in this category, are designed to create the appearance of security threats, and then they offer to fix them. A hardware keylogger is a physical device under your keyboard that you can only detect by physical inspection. Hence to save your private data chose the one which suit your needs. While for the most part employee monitoring is likely to be viewed as an intrusion, in a lot of ways it makes good business sense. Aside from being able to identify where you go, some spyware can capture keystrokes and hidden passwords, thus making them available to thieves or anyone who is willing to pay for this privileged information. As for the instant messaging, the major risk comes from accepting files from other users on the network. Such as black Friday virus, less than the scheduled time point perceived not to come out, wait until conditions possess the time was explosion spread from the destruction of the system. It is nice to make a short list of all the movie making software that you are interested in, but at the end of the day, you still need to narrow down your choice. The best way to find instructions to remove Trojan horse virus easily is to check out the top sites on the internet. Download and install a system scanner and run it in safe mode. It's for this reason that savvy business leaders hire public "relations" experts to build, polish, enhance, and protect their own reputations. Because this is a rogue antispyware program, you will probably see fake scans of your machine and frightening messages suggesting that youve been infected with malware.A Direct In Direction Of Straightforward Kaspersky Coupon Code 2020 Programs
by Hollis58V220236921 posted Oct 17, 2015
 Click here to find out more information on Danube River Cruises. When you 2015 Coupons for Kaspersky coupon Kaspersky loved this post and you want to receive more Kaspersky Kaspersky coupon promo code information with regards to Kaspersky promo code please visit our webpage. Only DNP can do the enormous weight change any overweight 2015 Coupons for Kaspersky individuals need. We've carried out reviews on all the leading security packages. The firewall function is very different from antivirus software. I will call you on Wednesday to work out the best plan for you." An action step has two parts: a what and a when. With this leading video converter software, you can do the job easily and reliably without having to spend money on any expensive video editing packages. With the internet finding replacement parts and aftermarket items for almost any vehicle has been made easy. Franklin has published his keys to personal and professional success in his book Access Now and now combines these lessons in leadership with his knowledge of the world of sports for the benefit of his alma mater. Let's see the basic configuration setup of the most important steps that you need to configure. As malware becomes more sophisticated and slows down your computer you need to be smart as well and take further steps to protect your identity and financial information while online. Spyware tracks the websites which the user visits and sends this information to web advertisers through which they send unwanted emails and pop-ups which are simply a nuisance to the web browsers. It prevents canine heartworm disease by eliminating the tissue state of heartworm larvae for 30 days after the infection, as well as for the treatment and control of ascarids and hookworms. Modern jeeps bear this similarity, and consumers appreciate the rough and rugged riding capabilities of such vehicles. It depends on the site that is being considered. I have done many case studies about cyber crimes and credit card theft in my college classes. Its important to restore registry so that the damage caused by the malware is counteracted. RegClean, and others in this category, are designed to create the appearance of security threats, and then they offer to fix them. A hardware keylogger is a physical device under your keyboard that you can only detect by physical inspection. Hence to save your private data chose the one which suit your needs. While for the most part employee monitoring is likely to be viewed as an intrusion, in a lot of ways it makes good business sense. Aside from being able to identify where you go, some spyware can capture keystrokes and hidden passwords, thus making them available to thieves or anyone who is willing to pay for this privileged information. As for the instant messaging, the major risk comes from accepting files from other users on the network. Such as black Friday virus, less than the scheduled time point perceived not to come out, wait until conditions possess the time was explosion spread from the destruction of the system. It is nice to make a short list of all the movie making software that you are interested in, but at the end of the day, you still need to narrow down your choice. The best way to find instructions to remove Trojan horse virus easily is to check out the top sites on the internet. Download and install a system scanner and run it in safe mode. It's for this reason that savvy business leaders hire public "relations" experts to build, polish, enhance, and protect their own reputations. Because this is a rogue antispyware program, you will probably see fake scans of your machine and frightening messages suggesting that youve been infected with malware.
Click here to find out more information on Danube River Cruises. When you 2015 Coupons for Kaspersky coupon Kaspersky loved this post and you want to receive more Kaspersky Kaspersky coupon promo code information with regards to Kaspersky promo code please visit our webpage. Only DNP can do the enormous weight change any overweight 2015 Coupons for Kaspersky individuals need. We've carried out reviews on all the leading security packages. The firewall function is very different from antivirus software. I will call you on Wednesday to work out the best plan for you." An action step has two parts: a what and a when. With this leading video converter software, you can do the job easily and reliably without having to spend money on any expensive video editing packages. With the internet finding replacement parts and aftermarket items for almost any vehicle has been made easy. Franklin has published his keys to personal and professional success in his book Access Now and now combines these lessons in leadership with his knowledge of the world of sports for the benefit of his alma mater. Let's see the basic configuration setup of the most important steps that you need to configure. As malware becomes more sophisticated and slows down your computer you need to be smart as well and take further steps to protect your identity and financial information while online. Spyware tracks the websites which the user visits and sends this information to web advertisers through which they send unwanted emails and pop-ups which are simply a nuisance to the web browsers. It prevents canine heartworm disease by eliminating the tissue state of heartworm larvae for 30 days after the infection, as well as for the treatment and control of ascarids and hookworms. Modern jeeps bear this similarity, and consumers appreciate the rough and rugged riding capabilities of such vehicles. It depends on the site that is being considered. I have done many case studies about cyber crimes and credit card theft in my college classes. Its important to restore registry so that the damage caused by the malware is counteracted. RegClean, and others in this category, are designed to create the appearance of security threats, and then they offer to fix them. A hardware keylogger is a physical device under your keyboard that you can only detect by physical inspection. Hence to save your private data chose the one which suit your needs. While for the most part employee monitoring is likely to be viewed as an intrusion, in a lot of ways it makes good business sense. Aside from being able to identify where you go, some spyware can capture keystrokes and hidden passwords, thus making them available to thieves or anyone who is willing to pay for this privileged information. As for the instant messaging, the major risk comes from accepting files from other users on the network. Such as black Friday virus, less than the scheduled time point perceived not to come out, wait until conditions possess the time was explosion spread from the destruction of the system. It is nice to make a short list of all the movie making software that you are interested in, but at the end of the day, you still need to narrow down your choice. The best way to find instructions to remove Trojan horse virus easily is to check out the top sites on the internet. Download and install a system scanner and run it in safe mode. It's for this reason that savvy business leaders hire public "relations" experts to build, polish, enhance, and protect their own reputations. Because this is a rogue antispyware program, you will probably see fake scans of your machine and frightening messages suggesting that youve been infected with malware.TAG •
Articles
- The Right Way To Increase Your English Language Vocabulary
- Must-Have Beauty Tips Each And Every Girl Need To Know
- Important Standards For Kaspersky Coupon Code 2016 - Wherever Toward Shift
- Asian Dating - You Can Locate The Perfect Partner
- When I First Moved Here
- Television / Movies :: Kim Kardashian Bio
- Cam Sexy Free - Three Shocking Facts About Free Sex Cams Told By An Expert
- The Importance Of Language Learning
-
 A Direct In Direction Of Straightforward Kaspersky Coupon Code 2020 Programs
A Direct In Direction Of Straightforward Kaspersky Coupon Code 2020 Programs
- Mpl Studios Talia - The Time Is Running Out! Think About These 8 Ways To Change Y...
- Nude Hot Women - 3 Odd-Ball Tips On Naked Girls Photos
- Choosing Effective Plans In Fire Raiders
- When There Is Constantly Snow And Dreadful Weather
- Are You A Gifted Person ? Check Out This Online Intelligence Test
- Free Live Nude Cam - The Unexplained Mystery Into Free Cam Broadcast Uncovered
- The Area Keeping Ux-Cd 600 Communications Core With Sharp Ux-Disc 600 Toner
- Dvd Can Be Read By Your Infant
- Kim Kardashian Mulls Surrogacy After 56 Pound Weight-loss: Fears Weight Gain
- Principles Of Fengshui For Your Bedroom - For Feng Shui For Your Bedroom Methods
- Prima Della Scarpe Hogan Contro La Sampdoria